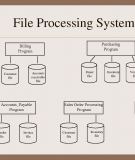
Accessing existing data
-
File processing is the process of creating, storing and accessing content of files. File processing can be used in opening saved files for read only purpose. It can be used to save a new file or displace the existing one. Through file processing you can make new files and save the existing files. You can also modify files through this process.
 1p
1p  sakuraphuong
sakuraphuong
 05-06-2013
05-06-2013
 75
75
 5
5
 Download
Download
-
A collection is a data structure – actually, an object – to hold other objects, which let you store and organize objects in useful ways for efficient access Check out the java.util package! Lots of interfaces and classes providing a general collection framework. Programmers may also provide implementations specific to their own requirements
 19p
19p  huanltgc00061
huanltgc00061
 05-05-2013
05-05-2013
 55
55
 2
2
 Download
Download
CHỦ ĐỀ BẠN MUỐN TÌM