
Secure Sockets
Secure Sockets
Overview of Lecture
Overview of Lecture
We covered an overview of authenticated key exchange protocols
In this lecture we will
–Look at issues related to Web Security
–Examine a specific implementation of such a protocol, known as
Secure Sockets
Web Security Issues
Web Security Issues
The Web has become the visible interface of the Internet
–Many corporations now use the Web for advertising, marketing and sales
Web servers might be easy to use but…
–Complicated to configure correctly and difficult to build without security
flaws
–They can serve as a security hole by which an adversary might be able to
access other data and computer systems
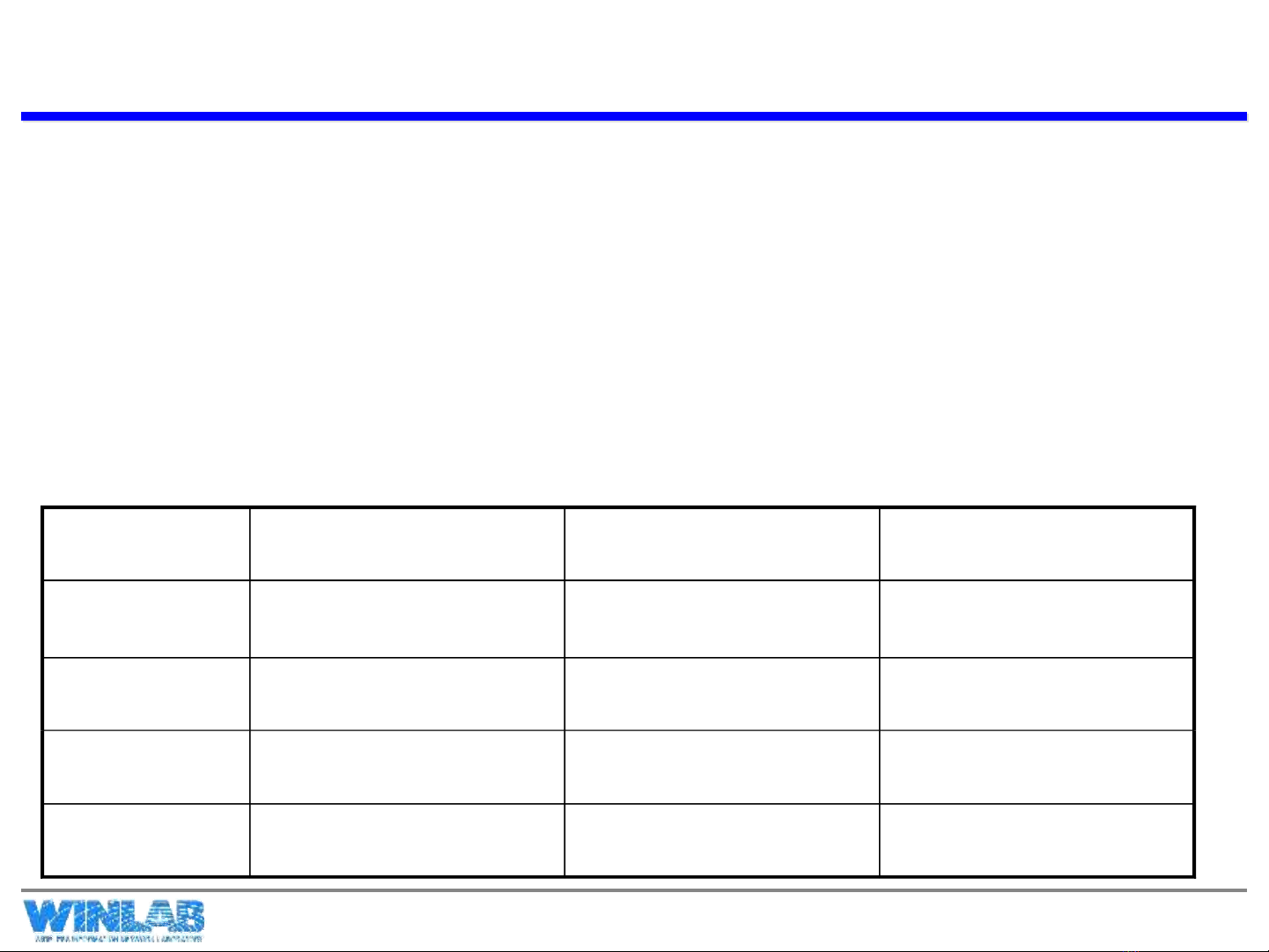
Threats Consequences Countermeasures
Integrity Modification of Data
Trojan horses
Loss of Information
Compromise of Machine
MACs and Hashes
Confidentiality Eavesdropping
Theft of Information
Loss of Information
Privacy Breach
Encryption
DoS Stopping
Filling up Disks and Resources
Stopped Transactions
Authentication Impersonation
Data Forgery
Misrepresentation of User
Accept false Data
Signatures, MACs
Table from Stallings, and from A. Rubin
So Where to Secure the Web?
So Where to Secure the Web?
There are many strategies to securing the web
1. We may attempt to secure the IP Layer of the TCP/IP Stack:
This may be accomplished using IPSec, for example.
2. We may leave IP alone and secure on top of TCP: This may be
accomplished using the Secure Sockets Layer (SSL) or
Transport Layer Security (TLS)
3. We may seek to secure specific applications by using
application-specific security solutions: For example, we may use
Secure Electronic Transaction (SET)
The first two provide generic solutions, while the third provides
for more specialized services
We will focus this lecture on SSL
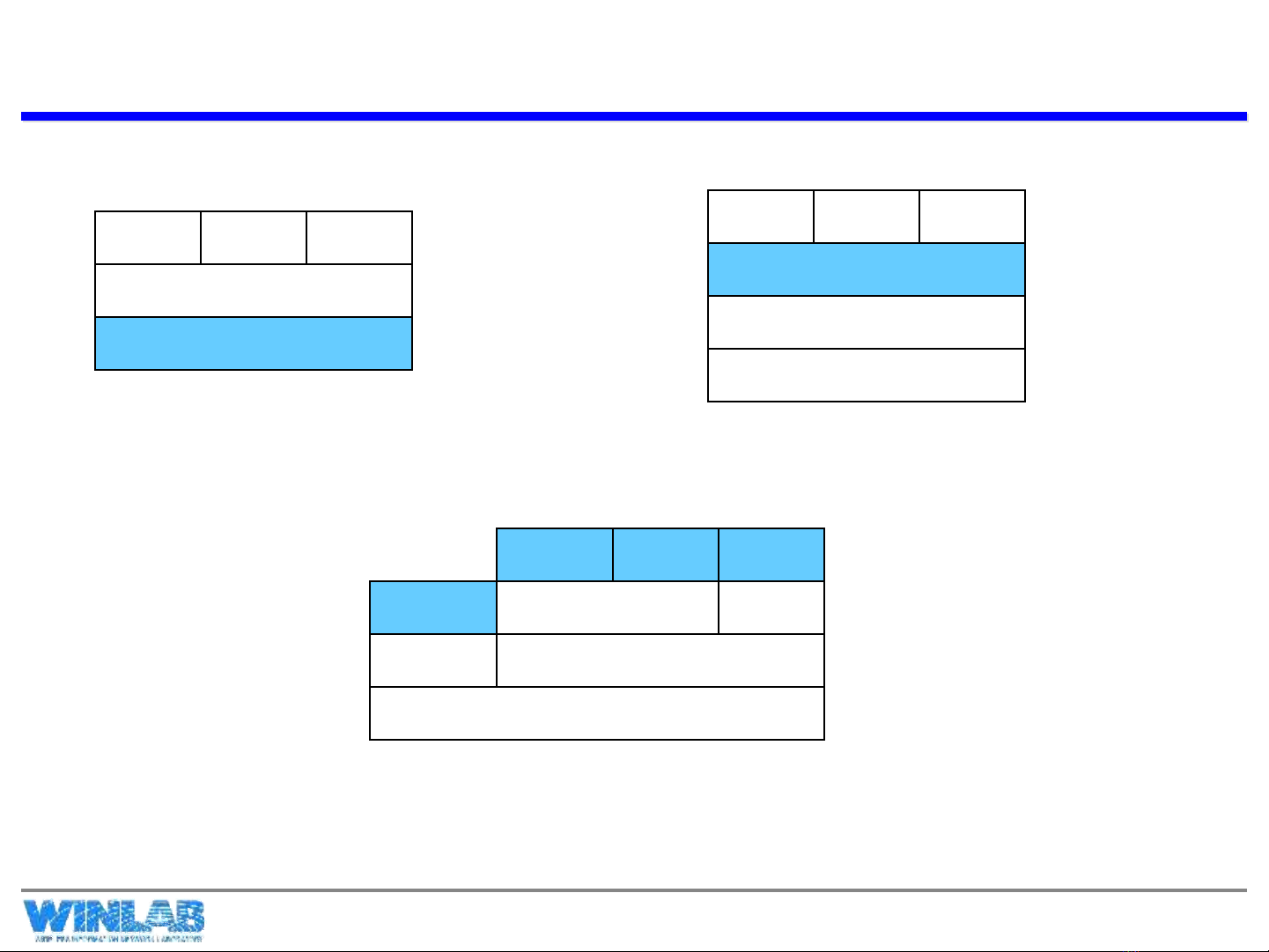
A Quick Look at Securing the TCP/IP Stack
A Quick Look at Securing the TCP/IP Stack
TCP
IP/IPSEC
HTTP FTP SMTP
TCP
IP
HTTP FTP SMTP
SSL/TLS
TCP
IP
S/MIME PGP
UDP
Kerberos SMTP
SET
HTTP
At the Network Level
At the Transport Level
At the Application Level




















![Câu hỏi ôn tập An toàn mạng [năm hiện tại]](https://cdn.tailieu.vn/images/document/thumbnail/2025/20250702/kimphuong555/135x160/56191751442800.jpg)

![Cẩm nang phòng chống, giảm thiểu rủi ro từ tấn công Ransomware [Mới nhất]](https://cdn.tailieu.vn/images/document/thumbnail/2025/20250627/vijiraiya/135x160/48331751010876.jpg)



