
Steganographic channels
Ho Dac Hung
1

Contents
•Problem
•Steganography by cover selection
•Steganography by cover synthesis
•Steganography by cover modification
2
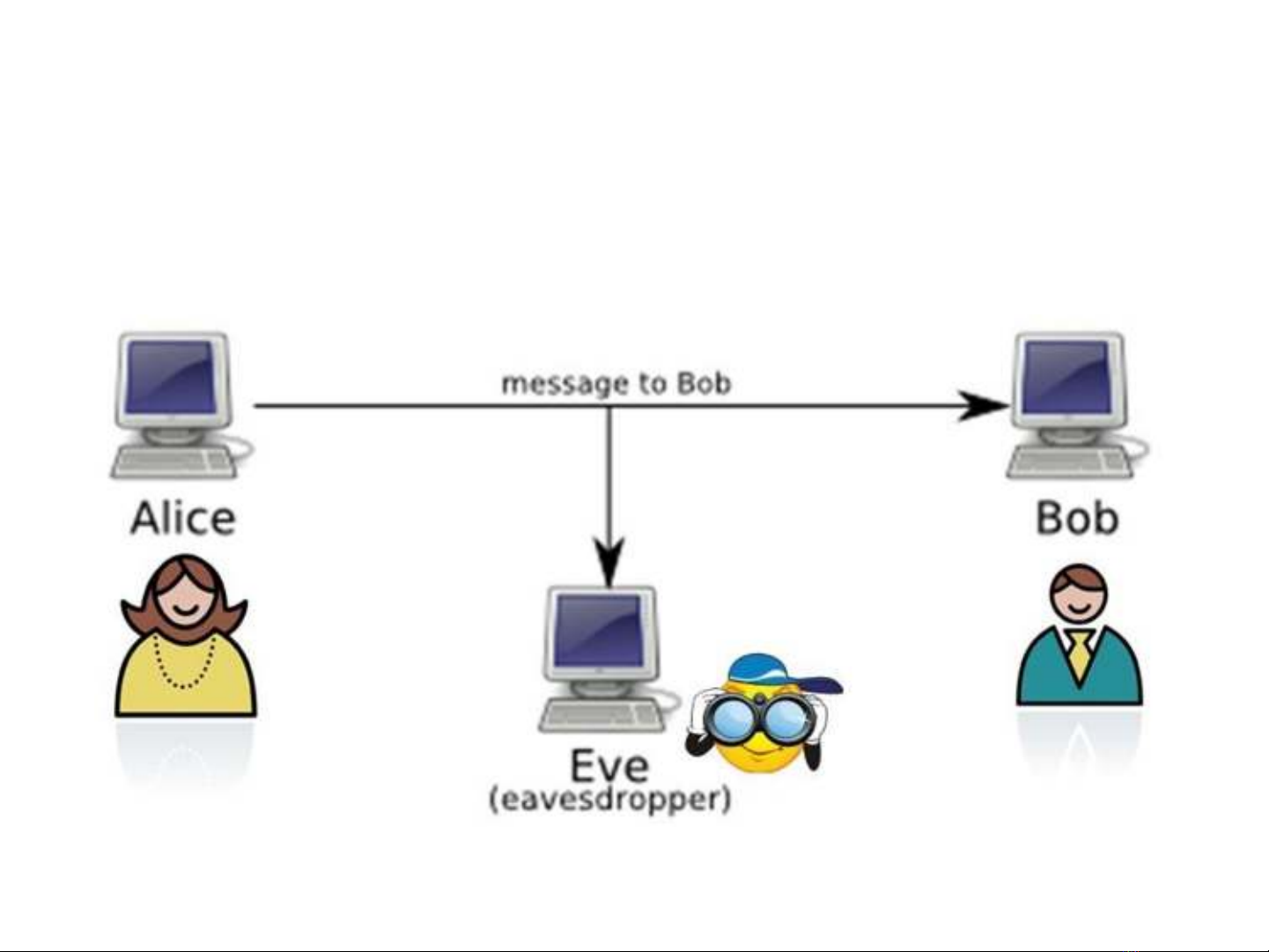
1. Problem
3
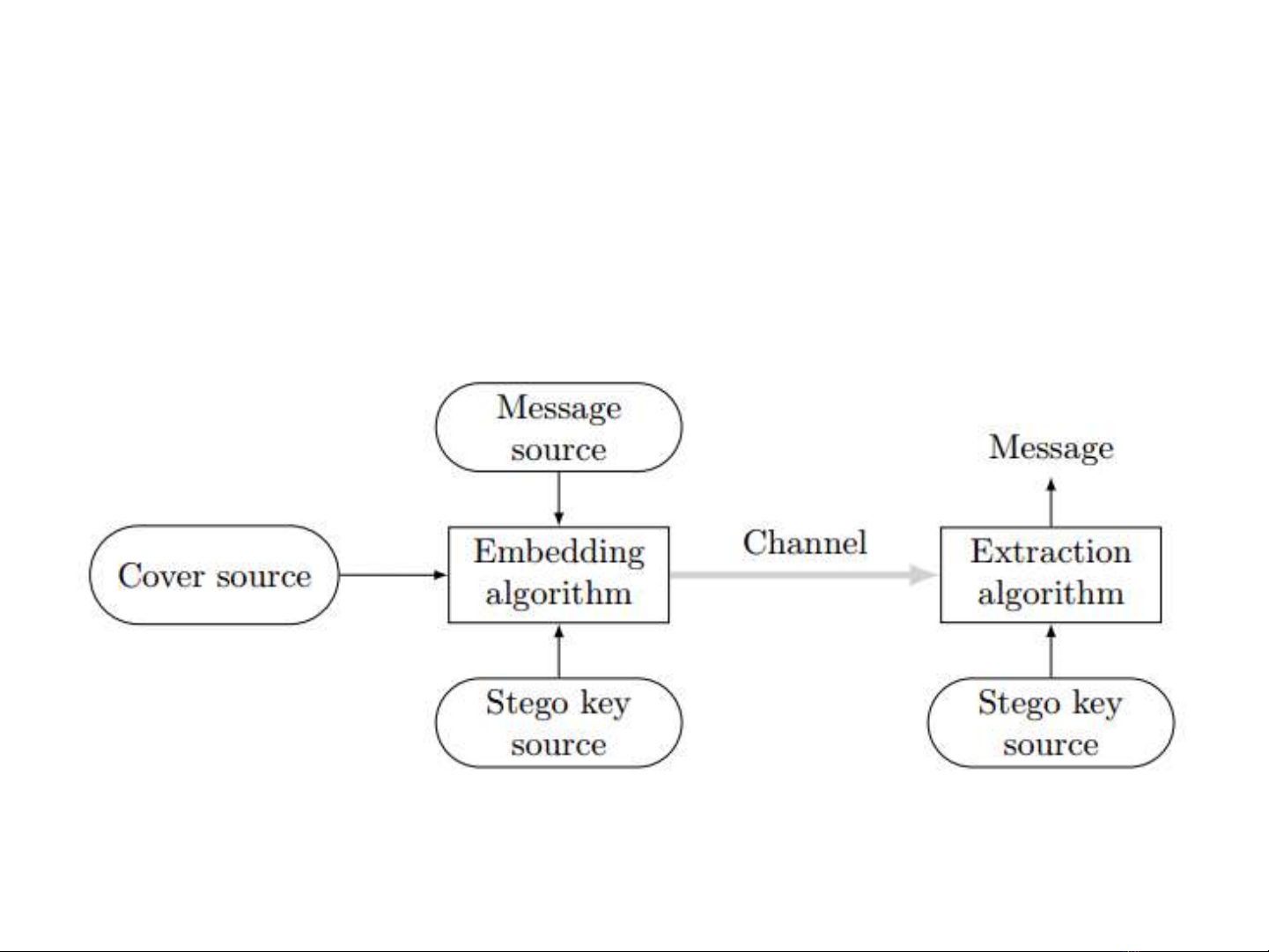
1. Problem
4

1. Problem
•Passive warden scenario
•Active warden scenario
•Malicious warden scenario
5





















![Câu hỏi ôn tập An toàn mạng [năm hiện tại]](https://cdn.tailieu.vn/images/document/thumbnail/2025/20250702/kimphuong555/135x160/56191751442800.jpg)

![Cẩm nang phòng chống, giảm thiểu rủi ro từ tấn công Ransomware [Mới nhất]](https://cdn.tailieu.vn/images/document/thumbnail/2025/20250627/vijiraiya/135x160/48331751010876.jpg)


