
Folder redirection can be seen as a subset of roaming profiles. By specifying an alternate location
for these folders on a network share, the user has access to these folders no matter which computer
he or she uses to log on.
Of the four folders that can be redirected, setting the My Documents folder for redirection is
probably the most advantageous. Not only will the user have his or her data available at any com-
puter, but storing this data on the server allows the data to be easily backed up to tape or other
offline storage media. As an administrator, you can also set quotas on server storage, helping to keep
the size of the My Documents folder in check.You can also take advantage of the offline folders
feature of Windows 2000 and Windows XP to keep the data available to users when they are not on
the network.
When setting up folder redirection, you should allow the system to create the folders in the
location where the data will be directed. A number of permissions must be set correctly to maintain
security on the redirected folders.Your best bet is to let the system handle this part of the process.
Folder redirection settings are located in the User Configuration area of the GPO under
Windows Settings.To enable redirection of one of the four folders, follow these steps:
1. Right-click the folder name and select Properties.
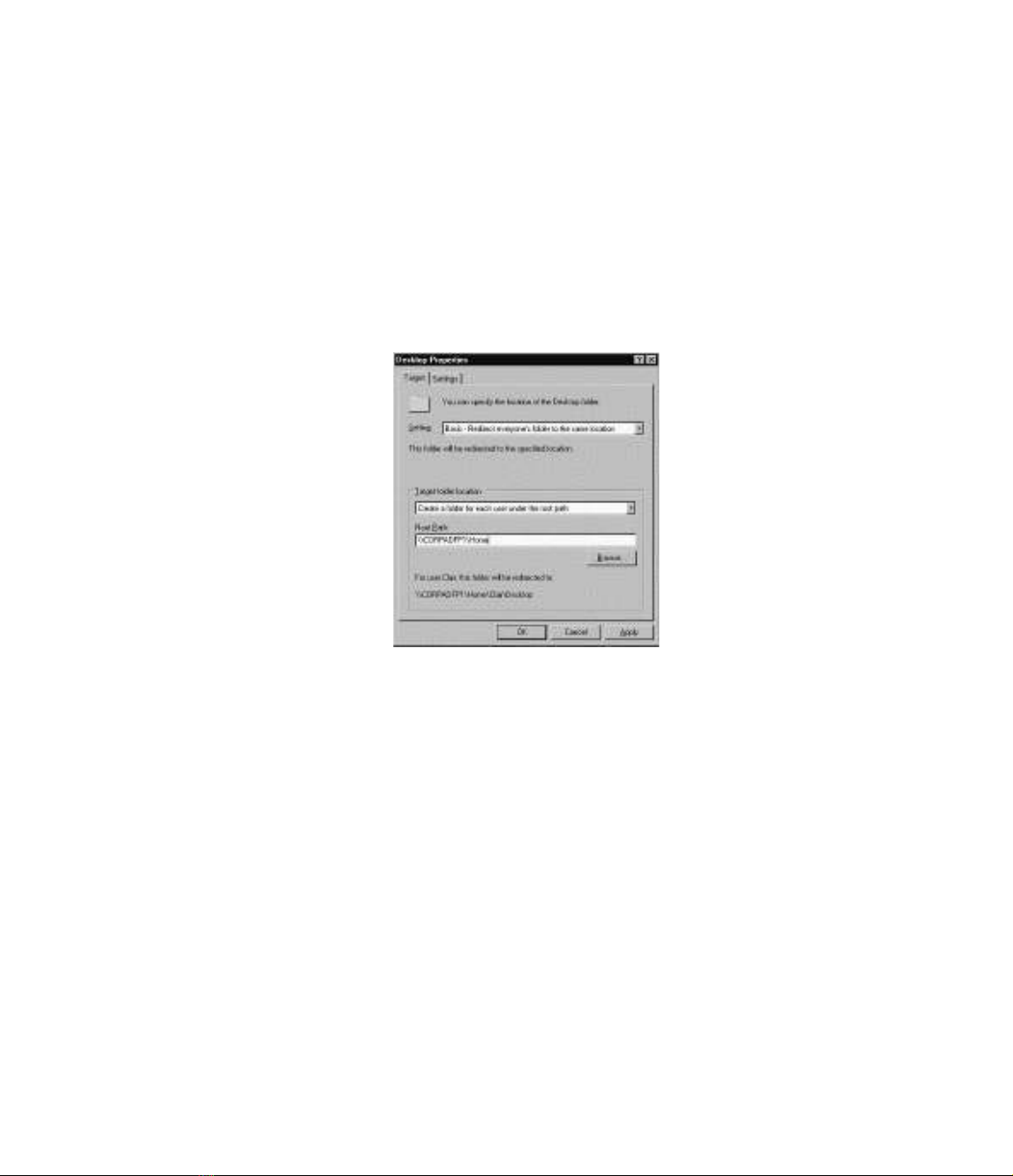
2. In the Target tab of the window, you can select the setting to use for redirection, as
shown in Figure 17.18.You can select between two options for the location of the redi-
rected folder.The basic option redirects the folder to the same folder path for all users. For
the Application Data and Desktop folders, there are three options for the folder location:
■Creating a directory for each user in the path specified
■Redirecting all users to the same location
■Pointing the folder to the local user profile location
586 Chapter 17 • Working with Group Policy in an Active Directory Environment
Figure 17.18 Selecting Options for Redirecting My Documents
If you choose to point the folder to the path in the user profile, the folder will point to the
default location as if no redirection had been applied. Redirecting the folder to a specific location
will create that location either on the network or on a local path, and all users who have this policy
applied will point to the same folder. For the Start Menu and Desktop folders, this might be a bene-
ficial setting, as you can centrally control the appearance and contents of those folders in one loca-
tion, but you need to be aware of the security settings on the folder.
The primary choice for this setting will probably be to create a folder for each user in a loca-
tion specified, as shown in Figure 17.19.As you can see, when the root path is specified, the dialog
box gives you an example of what the folder path will be.
The Start Menu and My Documents folders have slightly different options for redirection.
When redirecting the Start Menu, you do not have the option of specifying a unique path for each
individual user. Whether setting up basic or advanced redirection of the Start Menu, you can only
specify one common location for all users or redirect the folder back to the local user profile.
The Start Menu options are simpler than the Application Data and Desktop folder settings, but
the My Documents options are more complex. When redirecting the My Documents folder, there
are four location options for storing the folder. As with the Application Data and Desktop folders,
you can store the My Documents folder in the local user profile, a common directory for all users,
or have the system create a folder for each user in a common location.There is a fourth option,
however, for My Documents.That option allows you to redirect the My Documents folder to the
user’s home folder on the network.This option will not create a My Documents folder in the user’s
home folder. It will simply point the My Documents folder to the user’s home directory on the
network.
There are a few items you should pay attention to if you consider implementing this option.
First, you must have implemented the home folder settings for all users, and you must have created
those folders prior to implementing this option. Second, the security settings on the home folder are
not changed by the folder redirection policy, so you need to be aware of the settings applied to the
user home folder on the network. Finally, you have the choice of including the My Pictures folder
Working with Group Policy in an Active Directory Environment • Chapter 17 587
Figure 17.19 Setting the Folder Location for Redirection

with the redirected My Documents folder, or having the My Pictures folder stored in a different
location.This might be advisable if server disk storage is a concern. If you choose this option, the
My Pictures item in the My Documents folder will be a shortcut pointing to the correct location
for the actual folder.
The advanced option allows you to select the folder location based on security group.This is
one way to specify a different target location for the folder for different groups of users.You can set
multiple security groups to have different target locations within a single GPO in the domain.
Another way to accomplish this, especially if you only have a small set of users whose folders should
be redirected, is to set folder redirection GPOs at other locations within the directory and filter
access to those GPOs based on security.
When selecting the advanced redirection option, you can add the individual security groups for
redirection, and have the same choices for folder location as with the basic option. Setting advanced
folder redirection is functionally equivalent to setting up multiple GPOs with basic redirection settings
and security filtering.The difference is that there is only one GPO to manage instead of several.
Configuring User and Computer Security Settings
When browsing through the Group Policy Object Editor, you might have noticed that there are
security settings for both the user configuration and computer configuration. Some of these settings
are the same for both configurations, such as the Autoenrollment Settings for certificates discussed
earlier.There are many differences between the two options, however, and we cover some of those
differences in this section.
Computer Configuration
With these security settings, you can provide additional control and management over objects in the
directory.The settings contained in this area can govern how users authenticate to computers and
other resources on the network, can provide additional permissions or restrictions for resources in
the directory, can control audit settings, and can alter group membership.The settings in this area of
group policy are primarily used to specify alternate settings for specific computers on the network.
Table 17.2 lists the main option groups under Security Settings in the Computer Configuration
in the Group Policy Object Editor, along with a description of the security setting.
Table 17.2 Security Settings for Computer Configuration
Security Setting
Collection Description
Account Policies Contains setting groups for password policy settings, account
lockout settings, and Kerberos policy settings.
Local Policies Contains setting groups for auditing policy settings, user rights
assignment settings, and security options settings.
Event Log Contains settings for application, system, and security event logs.
Restricted Groups Contains groups for specific security restrictions.
588 Chapter 17 • Working with Group Policy in an Active Directory Environment
Continued
Table 17.2 Security Settings for Computer Configuration
Security Setting
Collection Description
System Services Contains settings for controlling startup and permissions for
system services.
Registry Keys Contains Registry keys and permissions to add.
File System Contains files or folders and permissions to add.
Wireless Network Contains policies governing specific wireless network connections.
Policies
Public Key Policies Contains setting groups for Encrypted File System policy settings,
Automatic Certificate Request settings, Trusted Root Certification
Authorities settings, and Enterprise Trust settings.
Software Restriction Contains settings, when enabled, for restricting access to certain
Policies software, such as 16-bit applications.
User Configuration
There are fewer options for configuring security settings in the User Configuration area of group
policy.The two groups of policies in this area are listed in Table 17.3.
Table 17.3 Security Settings for User Configuration
Security Setting
Collection Description
Public Key Policies Contains settings for certificate autoenrollment and Enterprise
Trust.
Software Restriction Contains settings that identify, through various means,
Policies applications that are authorized to run on a system.
Redirect the My Documents Folder
In this example, we walk through the process of redirecting the My Documents folder for a specific
group of users in the directory. We will take the Information Technology group and redirect their
folders to a shared location on the network, and use advanced redirection to limit folder redirection
only to members of that group. We will point the My Documents directory to a common location
and use the network’s home directory path as the root folder for the redirected folder.
1. Open Active Directory Users and Computers.
2. Right-click the domain container and select Properties.
3. Click the Group Policy tab and click New.
4. Name the policy Folder Redirection Policy and click Edit.
Working with Group Policy in an Active Directory Environment • Chapter 17 589

5. Under User Configuration, expand Windows Settings.
6. Expand Folder Redirection.
7. Right-click My Documents and select Properties.
8. In the Setting drop-down menu, select Advanced – Specify locations for various user
groups.
9. In the Security Group Membership pane, click Add.
10. In the Security Group Membership pane, enter the name of the security group, or
click Browse and find the group in the directory.This example uses the Information
Technology group.
11. In the Target Folder Location pane, select Create a folder for each user under the root
path from the drop-down menu.
12. Enter the UNC path to the desired folder in the Root Path field, or click Browse to find
the desired path.This example uses the path \\CORPADFP1\Home for the root path.
13. Click OK.
14. The My Documents Properties window should now appear as shown in Figure 17.20.
Click the Settings tab.
15. Make sure the check boxes for Grant the user exclusive rights to My Documents
and Move the contents of My Documents to the new location are enabled.
16. Click the Redirect the folder back to the local user profile location when policy
is removed option button.
17. The Settings tab should appear as shown in Figure 17.21. Click OK.
590 Chapter 17 • Working with Group Policy in an Active Directory Environment
Figure 17.20 Viewing the Redirection Settings for My Documents


























