http://www.iaeme.com/IJMET/index.asp 1645 editor@iaeme.com
International Journal of Mechanical Engineering and Technology (IJMET)
Volume 10, Issue 03, March 2019, pp. 1645–1654, Article ID: IJMET_10_03_166
Available online at http://www.iaeme.com/ijmet/issues.asp?JType=IJMET&VType=10&IType=3
ISSN Print: 0976-6340 and ISSN Online: 0976-6359
© IAEME Publication Scopus Indexed
METHOD FOR DETERMINATION OF THE
PROBABILITIES OF FUNCTIONING STATES
OF INFORMATION OF PROTECTION ON
CLOUD COMPUTING
Gulomov Sherzod Rajaboevich
Department of Providing Information Security, Tashkent University of Information
Technologies named after Muhammad al-Khwarizmi, Tashkent, Uzbekistan
Abdullaev Dilmurod Gulamovich
Department of Providing Information Security, Tashkent University of Information
Technologies named after Muhammad al-Khwarizmi, Tashkent, Uzbekistan
Nasrullaev Nurbek Bakhtiyorovich
Department of Providing Information Security, Tashkent University of Information
Technologies named after Muhammad al-Khwarizmi, Tashkent, Uzbekistan
Zokirov Odiljon Yoqubjon ugli
Department of Providing Information Security, Tashkent University of Information
Technologies named after Muhammad al-Khwarizmi, Tashkent, Uzbekistan
ABSTRACT
In this article the work of the components of information of protection tools on the
occurring violations, their types and the elimination of these violations and the possible
trajectory of a change over time of the functioning states of information of protection
tools with a discrete time are researched. Schemes for the transition of states of
information protection tools and a graph of probabilities of transitions between the
functioning states of information of protection tools with discrete time, allows for
detecting the vulnerabilities of information of protection tools are developed. Taking
into account the above, a method for determining the probabilities of states for the
functioning information of protection tools with discrete time allows describing a
graph-scheme of transitions using a small dimensionality of sets of states, to make a
square transition matrix at a lower bit depth is offered.
Key words: Discrete-time, possible trajectory, vulnerability, discrete mode, transition
probabilities, content filtering systems
Method For Determination of the Probabilities of Functioning States of Information of Protection
on Cloud Computing
http://www.iaeme.com/IJMET/index.asp 1646 editor@iaeme.com
Cite this Article: Gulomov Sherzod Rajaboevich, Abdullaev Dilmurod Gulamovich,
Nasrullaev Nurbek Bakhtiyorovich, Zokirov Odiljon Yoqubjon ugli, Method For
Determination of the Probabilities of Functioning States of Information of Protection
on Cloud Computing, International Journal of Mechanical Engineering and
Technology 10(3), 2019, pp. 1645-1654.
http://www.iaeme.com/IJMET/issues.asp?JType=IJMET&VType=10&IType=3
1. INTRODUCTION
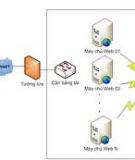
Cloud computing represents to use a large of technologies without physical connections. But
problem appears with sending information over the open network securely. Knowing the
probabilities of finding information of protection tools in various states allows you to predict
their behavior over time and identify the most likely conditions, which helps to focus the
security administrator's attention on less reliable components of information protection tools
and make more informed decisions on how to correct the violations.
For determine the probabilities of the state of functioning of various information of
protection tools, various mathematical methods are further applied, which use data on the
reliability of the components included in their composition. In this case, the choice of a specific
method depends, first of all, on the type of the considered information of protection tools - with
discrete or with continuous operation time.
For example, records from the work logs of information of protection system components
with discrete-time work about occurring violations, their types and about these violations
(automatically or by the administrator) are the source of data for the subsequent determination
of the reliability indicators of these components [1], consequently, the means discrete time
information. Naturally, such data should be sufficient in order to be able to determine with
acceptable accuracy the statistical estimates of indicators, that is, the samples must be
representative.
2. CLOUD SECURITY SERVICES
Cloud security specialists indicate that the report reflects the consensus of experts on the most
significant security threats in the cloud and focuses on threats stemming from the sharing of
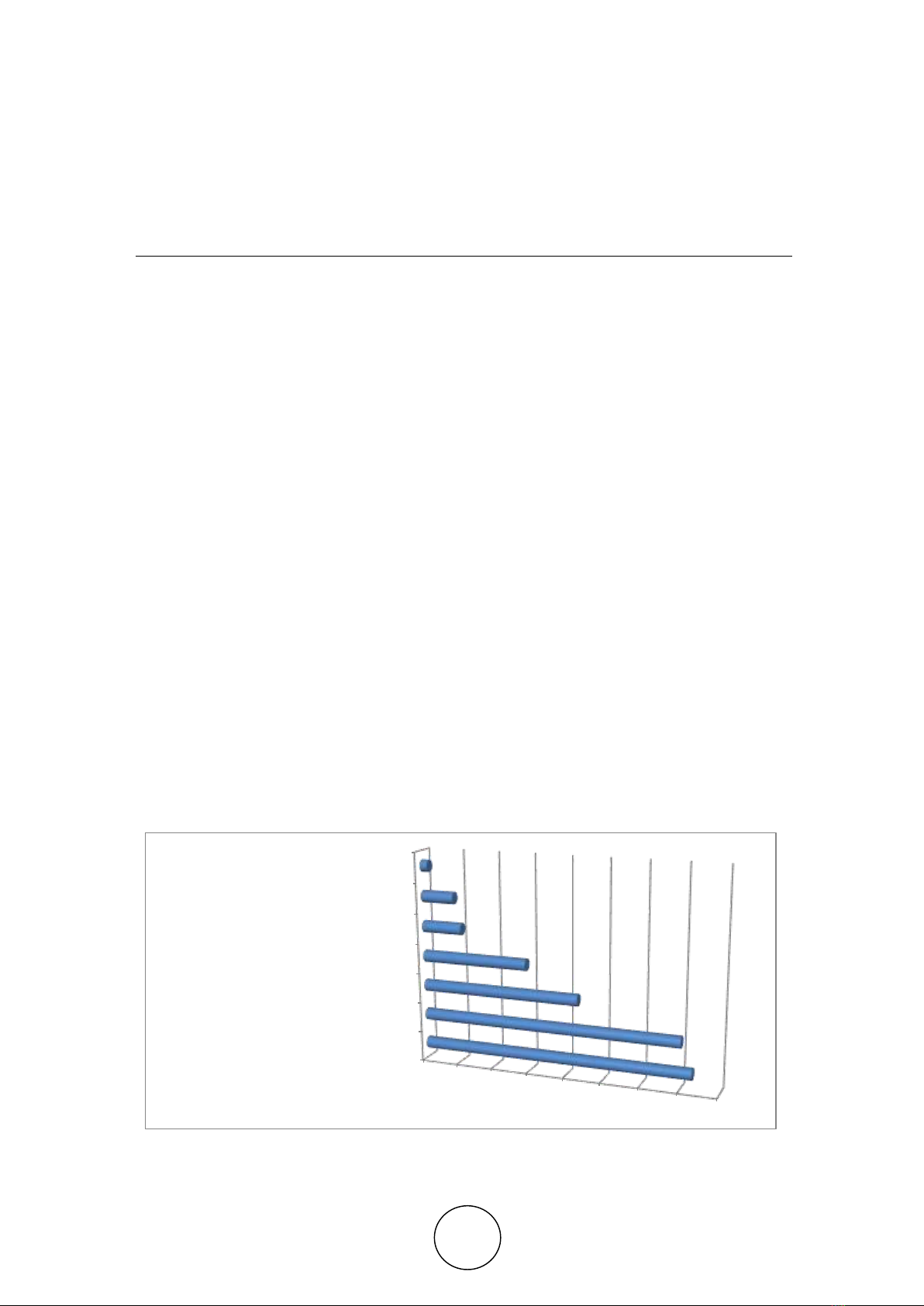
common cloud resources and access to them by multiple users on demand. In Fig.1 is shown
main barriers to implement cloud services.
Figure 1 The main barriers to implement cloud services
0% 10% 20% 30% 40% 50% 60% 70% 80%
No control on the channel and API for third party
No prepare to send confidential information
Difficulty to explain opportunity of the cloud services
Important to improve personal qualification
No work of cloud services for IT-personal
No barriers to implement
Financial barrier
Gulomov Sherzod Rajaboevich, Abdullaev Dilmurod Gulamovich, Nasrullaev Nurbek
Bakhtiyorovich, Zokirov Odiljon Yoqubjon ugli
http://www.iaeme.com/IJMET/index.asp 1647 editor@iaeme.com
In figure 1, we can see that cloud security specialists have more present of barriers and
problems on the information sending channel and cloud API. All cloud services have fallowing
threats: Data theft, data lost, account theft, hacking, unprotected interfaces and APIs, DDoS
attack, malicious insider, using of cloud resources by hackers, lacking of foresight, related
vulnerability, and cloud services can be slow.
To eliminate from these threats are used fallowing security services: Identity and access
management, data loss prevention, web security, e-mail security, security assessments,
intrusion management, security information and event management, encryption, business
continuity and disaster recovery, network security.
Also, for data exchanging over the network, we need to develop protected scheme. We offer
following recommendations:
As more companies store their data in the cloud and their employees use cloud services
more and more. IT specialists need to pay more attention to implementing more effective
mechanisms to control user access, such as multi-factor authentication. This is especially true
for companies that provide third parties and vendors with access to their data in the cloud.
Multi-factor authentication solutions can be centrally managed and provide more secure access
to all applications and data, whether they are hosted in the cloud or on the company's own
hardware.
IT specialists are able to fulfil their mission to protect corporate data and at the same time
act as a tool in the implementation of "Shadow it", implementing measures to ensure data
security, for example, introducing the approach “encryption-as-a-service”. This approach
allows to IT specialists to centrally manage data protection in the cloud, enabling other business
units to find and use cloud services as needed.
3. FORMULATION OF THE PROBLEM
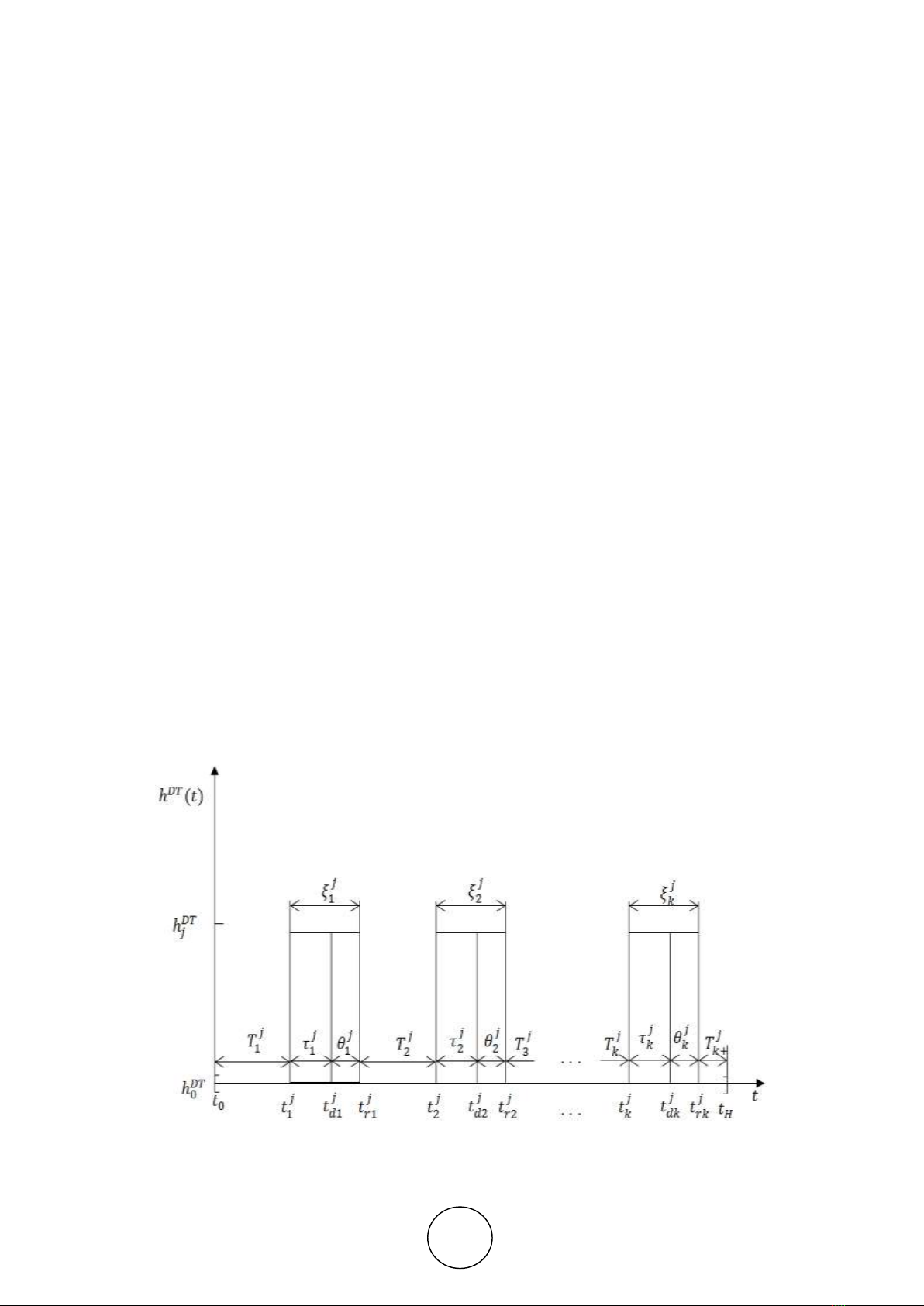
The trajectory of the change in time of the functioning state hDT(t) information of protection
tools with discrete-time work at a selected observation interval [t0,tH] in connection with the
appearance or elimination of a certain type of error, it can be represented as shown in Fig.2.
Figure 2 Possible trajectory of change in time of the functioning state hDT(t) information of
protection tools with discrete-time work
Method For Determination of the Probabilities of Functioning States of Information of Protection
on Cloud Computing
http://www.iaeme.com/IJMET/index.asp 1648 editor@iaeme.com
Here:
h0
DT - state of normal operation information of protection tools with discrete-time work;
hjDT - the state of the malfunction information of protection tools with discrete-time work due
to the i−th occurrence (i=1,k) j−th error (j=1,8) types;
tij- the moment of occurrence of the i−th error of the j−th type, taken from the first record of
the i-th error of the j−th type in the log;
tdi
j - the moment of the end of the search (detection) by the administrator of the i−th j−type
error and the start of its elimination, which is taken from the last entry in the log about the i−th
j-type error;
tri
j - the end of the elimination of the i−th error of the j-th type, taken from the record
characterizing the recovery of the component after the i−th error of the j−th;
Tij - random time between (i−l)−th and i−th errors of the j−th type, equal to Tij=tij−
tr(i−1)
j;
τij - random search time (detection) of the i−th error of the j−th type, equal to τij=tdi
j−tij; θij
- random time to eliminate the i−th error of the j−th type, equal to θij=tri
j−tdi
j;
ξij - random recovery time (search for errors and its elimination) component after the i−th error
in the j−th type, equal to ξij= tri
j−tij.
At the same time, in the information security tools with discrete operating time, the system
[2] behaviour (or, something the same, the system trajectory in phase space) is described by a
sequence of states.
For the effective functioning of vulnerability detection systems and content filtering
systems, it is necessary to monitor the information security of the protective equipment, which
determines the state changes at any time in the information-communication system. At the same
time, to identify the functioning states of information of protection tools with discrete-time
work, the following states are introduced hiDT (i=0…n) functioning, in which information of
protection tools with discrete-time work can be at an arbitrary point in time.
An example:
Table 1 Possible functioning state of information of protection tools with discrete-time work
State Description
h0
DT
the normal functioning of information of protection tools with discrete-time work
h1
DT
associated with the inability to obtain updates of the knowledge base of information of
protection tools with discrete-time work.
h2
DT
associated with the lack of information of protection tools with discrete-time work of
the rights to network access to servers, performed special procedures for detecting
events that affect in the information-communication system.
h3
DT
failure of information of protection tools with discrete-time work associated with a
malfunction of the physical server on which information of protection tools with
discrete-time work are deployed.
h4
DT
failure of information of protection tools with discrete-time work due to the
impossibility of saving the results of special procedures performed.
h5
DT
a condition characteristic of an incorrectly completed operation of the index server.
h6
DT
the state is characteristic of the ceased to respond to the controls of the indexing server.
h7
DT
the state is characteristic of information of protection tools with discrete-time work,
when the agent cannot copy files from the information security database with
continuous operation time in the storage of information of protection tools with discrete-
time work due to unavailability of the network drive on which it is located.
Gulomov Sherzod Rajaboevich, Abdullaev Dilmurod Gulamovich, Nasrullaev Nurbek
Bakhtiyorovich, Zokirov Odiljon Yoqubjon ugli
http://www.iaeme.com/IJMET/index.asp 1649 editor@iaeme.com
P2.1
ℎ2.1
𝐷𝑇
ℎ1𝐷𝑇
ℎ2
𝐷𝑇
P01
P02
h8
DT
the state characterizes the work of information of protection tools with discrete-time
work, when the agent cannot copy information of protection tools with discrete-time
work of files from the database of other information of protection tools into the storage
due to unsuccessful authentication of the module into the information of protection tools
database.
…
…
4. SCHEMES FOR THE TRANSITION OF STATES OF INFORMATION
OF PROTECTION TOOLS
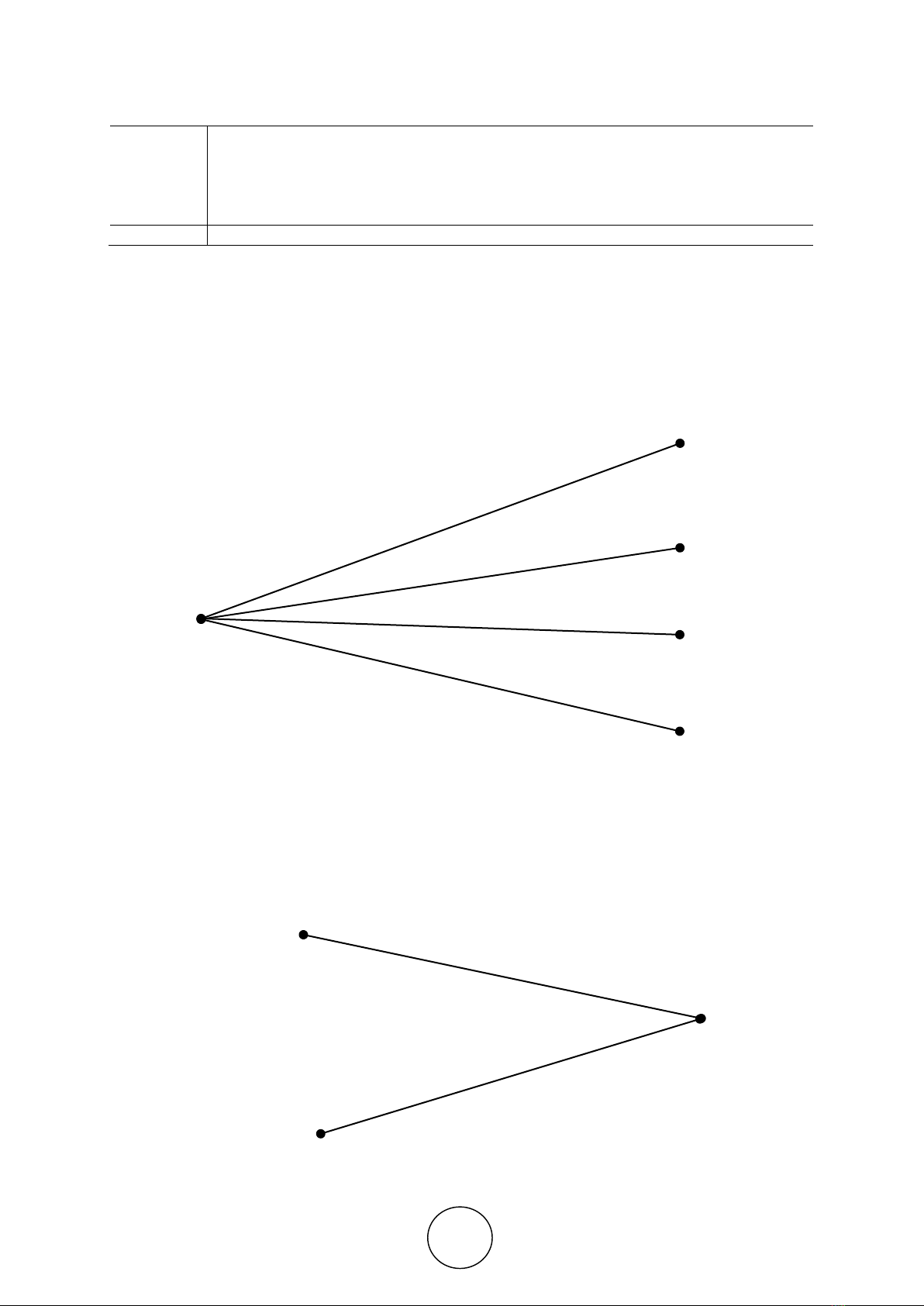
In Fig.3 is shown an exemplary scheme transition of states of information of protection tools,
where h0
DT – is the initial and normal functioning state and h1
DT – is a state when a violation
occurs in the process of functioning of the funds.
Figure 3 The scheme transition from one state to another
Furthermore, it can also enter hi.i
DT the functioning states of information of protection tools
with discrete-time work [3], in which the transition from the states hiDT (in this case h1
DT - h8
DT),
characterized by the violation of the functions of one of the components i, to the states
associated with the violation as well the functions of the other component i (Fig.4).
Figure 4 The scheme of the emergence of new united events
P00
ℎ0
𝐷𝑇
ℎ1𝐷𝑇
ℎ2
𝐷𝑇
…
ℎ𝑖𝐷𝑇
P01
P02
…
P𝑖