Microsoft ISA Server 2004 Firewall
Microsoft ISA Server 2004 is a hybrid stateful packet-inspecting, circuit-filtering, and
application layer proxy firewall. By hybrid, we mean that it can provide any of those
functionalities at any given time based on the traffic it is receiving. If it has an application
filter for the given protocol or application, it will function as an application proxy
firewall for that traffic. If it does not, it will resort to either stateful packet inspecting or
circuit filtering as required. In addition, ISA Server 2004 includes virtual private
networking (VPN) and caching capabilities, allowing it to function as an all-in-one
device that, as one would expect, integrates pretty cleanly with Microsoft-centric
environments.
Before we look at the features of Microsoft ISA Server 2004, let's talk about the elephant
in the room, namely the perception that ISA Server 2004 is not a "real" firewall. This
perception is largely the result of misinformation, lack of education regarding the
product, and simple dislike/disregard of anything Microsoft being remotely considered as
a security solution. When you look at ISA Server 2004 with an honest and skeptical eye,
it is relatively easy to cut through many of the fallacies and realize that Microsoft ISA
Server 2004 is an effective and practical firewall solution.
First on the list of misconceptions is the statement that any firewall running on a
Windows platform cannot be secure. This is just not factually accurate. All firewalls run
on some operating system. In the case of firewalls such as the Cisco PIX Firewall or
Check Point SecurePlatform, the operating system is specialized and hardened for use on
a firewall. Windows, out of the box, is not designed to be run on a firewall, but it can be
effectively secured and hardened following the principles of running the minimum
required services and functionality necessary to operate as a firewall alone. Some
excellent resources detail how to effectively secure the underlying Windows operating
system:
• NSA Security Configuration Guides
http://www.nsa.gov/snac/downloads_all.cfm?MenuID=scg10.3.1
• Hardening the Windows Infrastructure on the ISA Server 2004 Computer
http://www.microsoft.com/technet/prodtechnol/isa/2004/plan/hardeningwindows.
mspx
• Windows Server 2003 Security Guide
http://www.microsoft.com/technet/security/prodtech/windowsserver2003/w2003h
g/sgch00.mspx
• ISA Server 2004 Security Hardening Guide
http://www.microsoft.com/technet/prodtechnol/isa/2004/plan/securityhardeninggui
de.mspx
Note
Keep in mind that many of the procedures for Windows 2000 are applicable to Windows
2003 and vice versa, so do not hesitate using both the Windows 2000 and 2003 guides
regardless of your actual operating system
Another frequent misconception is that ISA Server 2004 is "just" an upgrade to Microsoft
Proxy Server 2.0. Although ISA Server 2004 is indeed the logical upgrade to Proxy
Server 2.0 (technically, ISA Server 2000 is the direct upgrade to Proxy Server 2.0), that is
not to say that ISA Server 2004 is just a proxy server. Proxy Server 2.0 had absolutely no
advanced firewall features. It was primarily a caching engine with basic packet-filtering
capabilities. Microsoft ISA Server 2004 is a fully featured firewall, capable of performing
stateful packet inspection as well as application layer filtering and proxying. In addition,
it can function as a caching engine. Simply put, trying to claim that because ISA Server
2004 is an upgrade to Proxy Server it is therefore not a "real" firewall has absolutely no
technical merit.
Microsoft ISA Server 2004 Features
Microsoft ISA Server 2004 consists of two editions: Standard Edition and Enterprise
Edition. The predominant differences between the Standard and Enterprise editions relate
to scalability. Table 8-1 summarizes the differences between the Standard and Enterprise
editions.
Table 8-1. Comparison of ISA Server 2004 Standard and Enterprise Editions
Feature Standard Edition Enterprise Edition
Networks Unlimited Unlimited, with the addition
of enterprise networks
(networks that can be applied
to any firewall array anywhere
in the enterprise)
Scale up Up to 4 CPUs and 2-GB RAM Unlimited (per operating
system)
Scale out Single server Up to 32 nodes using
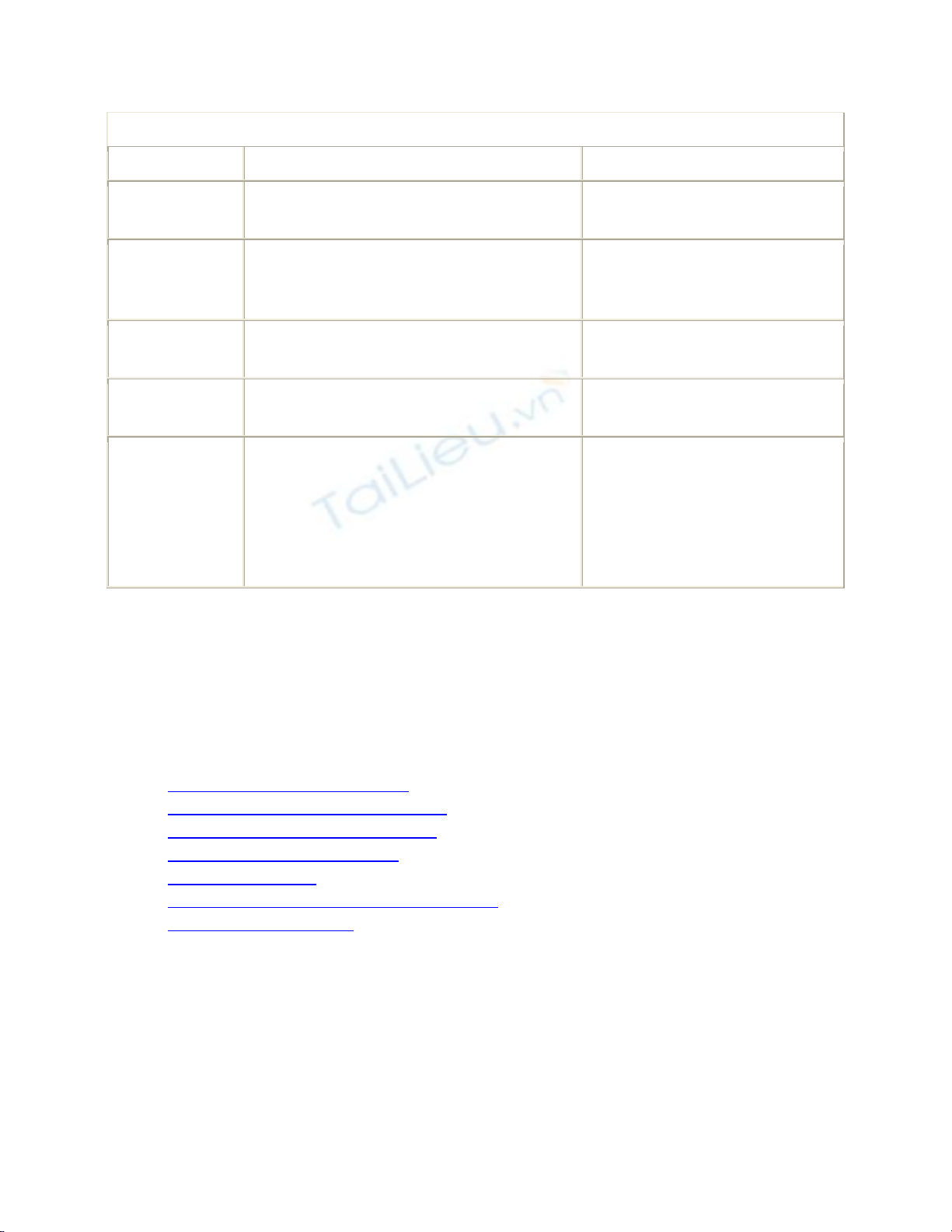
Table 8-1. Comparison of ISA Server 2004 Standard and Enterprise Editions
Feature Standard Edition Enterprise Edition
Microsoft Network Load
Balancing (NLB)
Caching Single server store Unlimited (through the use of
Cache Array Routing Protocol
(CARP))
High
availability None Yes (using NLB)
Management Local management and configuration Array and enterprise-level
configuration
Underlying
operating
system
Microsoft Windows Server 2003
(Standard or Enterprise Edition),
Microsoft Windows 2000 Server or
Advanced Server with Service Pack 4
(SP4) or later, or Windows 2000
Datacenter Server
Microsoft Windows Server
2003 (Standard or Enterprise
Edition)
As you can see, if you need multiple ISA servers working in tandem, or need additional
memory and processors, you need to use the Enterprise Edition. Similarly, if you need a
high-availability solution, use Enterprise Edition.
In general, Microsoft ISA Server 2004's firewall features can be categorized as follows:
• Security and filtering features
• Firewall clients and authentication
• Web caching server functionality
• Network services publishing
• VPN functionality
• Management and administration features
• Miscellaneous features
Security and Filtering Features
The Microsoft ISA Server 2004 firewall is a hybrid firewall capable of performing the
following:
• Stateful packet inspection ISA Server 2004 can perform full stateful packet
inspection and filtering of all traffic passing through the firewall.

• Circuit filtering ISA Server 2004 can perform application-transparent circuit
filtering to a host of protocols, including Telnet, RealAudio, Windows Media
technologies, and Internet Relay Chat (IRC). This filtering occurs at the transport
or session layer as opposed to the application layer. This proxy functionality
works in conjunction with the stateful packet-inspection functionality.
• Application filtering ISA Server 2004 can act as an application proxy and filter
traffic for a number of protocols including HTTP, FTP, and Gopher. This allows
Microsoft ISA Server 2004 to act on behalf of clients, hiding and protecting the
client from external resources and threats.
Microsoft ISA Server 2004 can perform these filtering functions in a multidirectional
method, supporting as many network interfaces as the physical hardware can contain.
This allows for the creation of multiple demilitarized (DMZ) segments, allowing for the
creation of unique filtering rulesets on a per-DMZ segment basis. Of course, filtering of
traffic for/from the internal and external networks is also available.
Microsoft ISA Server 2004 also supports basic intrusion detection functionality, although
full intrusion detection system (IDS) functionality is best provided through the
integration of third-party products such as ISS RealSecure or similar products. Currently,
ISA Server 2004 can natively detect the following intrusion/attack attempts:
• WinNuke
• Ping of death
• Land attack
• IP half scan
• Port scan
• UDP bomb
• POP3 buffer overflow
• SMTP buffer overflow
• DNS zone transfer
• DNS length overflow
• DNS host name overflow
Firewall Clients and Authentication
Microsoft ISA Server 2004 supports the following three types of firewall clients for
systems that are attempting to access resources outside the protected network:
• SecureNAT client
• Firewall client
• Web proxy client

![Đề thi cuối kì Nhập môn Mạng máy tính: Tổng hợp [Năm]](https://cdn.tailieu.vn/images/document/thumbnail/2025/20251110/nminhthoi53@gmail.com/135x160/38281762757217.jpg)
![Câu hỏi ôn tập An toàn mạng môn học: Tổng hợp [mới nhất]](https://cdn.tailieu.vn/images/document/thumbnail/2025/20250919/kimphuong1001/135x160/30511758269273.jpg)















![Sổ tay Kỹ năng nhận diện & phòng chống lừa đảo trực tuyến [Mới nhất]](https://cdn.tailieu.vn/images/document/thumbnail/2025/20251017/kimphuong1001/135x160/8271760665726.jpg)
![Cẩm nang An toàn trực tuyến [Mới nhất]](https://cdn.tailieu.vn/images/document/thumbnail/2025/20251017/kimphuong1001/135x160/8031760666413.jpg)






