Virtual addresses
-
This study aims to investigate how to maximize the opportunities that allow Bitcoin in contributing for Indonesia tax revenue and also, the respond to the growing issues of virtual money transactions in the world. This study uses Literature study method based on some previous research and scientific journals that discuss about Bitcoin as a means of payment in sale and purchase transactions. The results of this study Bitcoin transaction tax still needs to be addressed is the absence of Legal Basis and legislation on legality of Bitcoin as a recognized payment instrument in Indonesia.
 5p
5p  longtimenosee09
longtimenosee09
 08-04-2024
08-04-2024
 2
2
 0
0
 Download
Download
-
Ebook "Insider attack cyber security beyond the hacker" includes content: The insider attack problem nature and scope; reflections on the insider threat; a survey of insider attack detection research; naive bayes as a masquerade detector - addressing a chronic failure; towards a virtualization enabled framework for information traceability,... and other contents.
 228p
228p  longtimenosee08
longtimenosee08
 31-03-2024
31-03-2024
 5
5
 1
1
 Download
Download
-
Ebook Managing Cisco network security: Part 1 includes contents: Chapter 1 introduction to IP network security, chapter 2 traffic filtering on the Cisco IOS, chapter 3 network address translation (NAT), chapter 4 Cisco PIX Firewall, chapter 5 virtual private networks.
 257p
257p  longtimenosee05
longtimenosee05
 31-03-2024
31-03-2024
 2
2
 0
0
 Download
Download
-
Ebook "Gas sensing fundamentals (Springer series on Chemical sensors and biosensors, Volume 15)" addresses various basic sensor principles, covers micro gravimetric sensors, semiconducting and nano tube sensors, calorimetric sensors and optical sensors. Furthermore, the authors discuss recent developments in the related sensitive layers including new properties of nano structured metal oxide layers.
 348p
348p  tudohanhtau1006
tudohanhtau1006
 29-03-2024
29-03-2024
 2
2
 1
1
 Download
Download
-
Ebook Configuring Juniper Networks NetScreen & SSG Firewalls: Part 2 includes content: Chapter 8: address translation, chapter 9: transparent mode, chapter 10: attack detection and defense, chapter 11: VPN theory and usage, chapter 12: high availability, chapter 13: troubleshooting the juniper firewall, chapter 14: virtual systems.
 356p
356p  longtimenosee03
longtimenosee03
 22-02-2024
22-02-2024
 7
7
 2
2
 Download
Download
-
Ebook Beginning ethical hacking with python: Part 2 includes contents: Chapter 15: classes; chapter 16: string methods; chapter 17: file input and output; chapter 18: containers; chapter 19: database; chapter 20: module; chapter 21: debugging, unittest module; chapter 22: socket and networking; chapter 23: importing nmap module; chapter 24: building an nmap network scanner; chapter 25: protect anonymity on the internet; chapter 26: dark web and tor; chapter 27: proxy chains; chapter 28: virtual private network or VPN; chapter 29: MAC address.
 128p
128p  haojiubujain010
haojiubujain010
 14-12-2023
14-12-2023
 6
6
 2
2
 Download
Download
-
Part 1 of ebook "The virtual utility: Accounting, technology and competitive aspects of the emerging industry" provides readers with contents including: historic and strategic perspective, from monopoly service to virtual utility; the virtual utility, strategic and managerial perspectives, welcoming address; the virtual utility, planning and strategic investment analysis; justifying capital investments in the emerging electric utility, accounting for an uncertain and changing industry structure;...
 141p
141p  mocthanhdao0210
mocthanhdao0210
 19-11-2023
19-11-2023
 5
5
 4
4
 Download
Download
-
Ebook Information Storage and Management: Part 1 includes the following content: Chapter 1: Introduction to Information Storage and Management; Chapter 2: Storage System Environment; Chapter 3: Data Protection: RAID; Chapter 4: Intelligent Storage System; Chapter 5: Direct-Attached Storage and Introduction to SCSI; Chapter 6: Storage Area Networks; Chapter 7: Network-Attached Storage; Chapter 8: IP SAN; Chapter 9: Content-Addressed Storage; Chapter 10: Storage Virtualization.
 248p
248p  haojiubujain01
haojiubujain01
 24-06-2023
24-06-2023
 9
9
 4
4
 Download
Download
-
This thesis addresses important issues about how to make game characters and virtual agents more realistic or believable by using cognitive-social personality theories. We begin motivation by discussing two examples. The first is from a television series and the second is a more concrete example that will be used throughout the thesis to explain concepts and the model. These examples represent the ideal goal of our work.
 261p
261p  runthenight07
runthenight07
 01-03-2023
01-03-2023
 4
4
 2
2
 Download
Download
-
Ebook Information storage and management: Storing, managing, and protecting digital information - Part 1 include of the following content: Chapter 1: Introduction to Information Storage and Management; Chapter 2: Storage System Environment; Chapter 3: Data Protection: RAID; Chapter 4: Intelligent Storage System; Chapter 5: Direct-Attached Storage and Introduction to SCSI; Chapter 6: Storage area networks; Chapter 7: Network-Attached Storage; Chapter 8: IP SAN; Chapter 9: Content-Addressed Storage; Chapter 10: Storage Virtualization.
 248p
248p  runthenight03
runthenight03
 07-12-2022
07-12-2022
 16
16
 5
5
 Download
Download
-
Advanced Computer Architecture - Lecture 33: Memory hierarchy design. This lecture will cover the following: virtual memory system; virtual memory address translation; virtual memory performance; protection of multiple processes sharing memory; VM address translation concept; fast address translation;...
 53p
53p  haoasakura
haoasakura
 30-05-2022
30-05-2022
 11
11
 3
3
 Download
Download
-
Advanced Computer Networks: Lecture 45. This lecture will cover the following: global internets; diameter of the internet; internet structure today; multiple backbone service providers; arbitrary graph structure; virtual geographies; scaling problems for the internet; IP address hierarchy evolution;...
 485p
485p  haoasakura
haoasakura
 30-05-2022
30-05-2022
 15
15
 3
3
 Download
Download
-
Advanced Operating Systems - Lecture 23: Goals of OS memory management. This lecture will cover the following: Goals of OS memory management; questions regarding memory management; multiprogramming; virtual addresses; fixed partitioning; variable partitioning; fragmentation;...
 21p
21p  haoasakura
haoasakura
 30-05-2022
30-05-2022
 13
13
 3
3
 Download
Download
-
Advanced Operating Systems - Lecture 24: Modern technique -Paging. This lecture will cover the following: paging; address translation; page tables and page table entries; multi-level address translation; page faults and their handling;...
 20p
20p  haoasakura
haoasakura
 30-05-2022
30-05-2022
 9
9
 3
3
 Download
Download
-
Lecture Computer networks: Lesson 24 - Hammad Khalid Khan. The main topics covered in this chapter include: address for the virtual internet, the IP addressing scheme, the IP address hierarchy, original classes of IP addresses,...
 10p
10p  youzhangjing_1909
youzhangjing_1909
 28-04-2022
28-04-2022
 17
17
 3
3
 Download
Download
-
Lecture Computer networks: Lesson 29 - Hammad Khalid Khan. The main topics covered in this chapter include: IP datagrams and datagram forwarding, fundamental internet communication service, connectionless service, virtual packets, IP datagram size, routing tables & address masks,...
 21p
21p  youzhangjing_1909
youzhangjing_1909
 28-04-2022
28-04-2022
 18
18
 2
2
 Download
Download
-
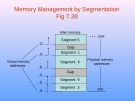
Lecture Advanced computer architecture: Lesson 40. The main topics covered in this chapter include: virtual memory, memory management system, memory management and address translation, memory management using segmentation, segmentation mechanism, page replacement,...
 20p
20p  wangziyi_1307
wangziyi_1307
 26-04-2022
26-04-2022
 13
13
 3
3
 Download
Download
-
Lecture Windows programming - Lesson 24: Memory management basics. The main topics covered in this chapter include: separate address space for a process, physical and virtual memory, page table, address space: linear and physical address, committed and reserved pages, same address in different processes may map to different things or nothing,...
 16p
16p  wangziyi_1307
wangziyi_1307
 26-04-2022
26-04-2022
 14
14
 2
2
 Download
Download
-
Functional communication is vital in many areas of daily life, and modifying dysfunctional communication has been emphasized in various social areas, including family and school. The present preliminary study addressed the feasibility of a virtual reality (VR)-based interactive feedback program for the modification of dysfunctional communication.
 11p
11p  vigeorgia2711
vigeorgia2711
 30-11-2020
30-11-2020
 16
16
 2
2
 Download
Download
-
Chapter 26 - Virtual private networks and network address translation. Upon completion you will be able to: Understand the difference between an internet and an extranet, understand private, hybrid, and virtual private networks, understand how VPN can guarantee privacy, understand the mechanism of NAT.
 15p
15p  nanhankhuoctai10
nanhankhuoctai10
 23-07-2020
23-07-2020
 21
21
 2
2
 Download
Download
CHỦ ĐỀ BẠN MUỐN TÌM